Uncategorized
Implement Local SEO Fixes for Lagos: Beat Google Maps Competitors

Local SEO for Lagos: 5 Website Arrangement Fixes That Beat Competitors on Google Maps
When your business operates in a competitive market like Lagos, standard search engine optimization (SEO) offers limited value. Your potential customers are looking for you now, and they are often using their phones to search for services “near me.” When your website’s arrangement is faulty, you miss the crucial opportunity to appear prominently on Google Maps and in the local search pack. Honestly, you must consider the technical arrangement of your site as the most vital layer of your local SEO fixes for Lagos.
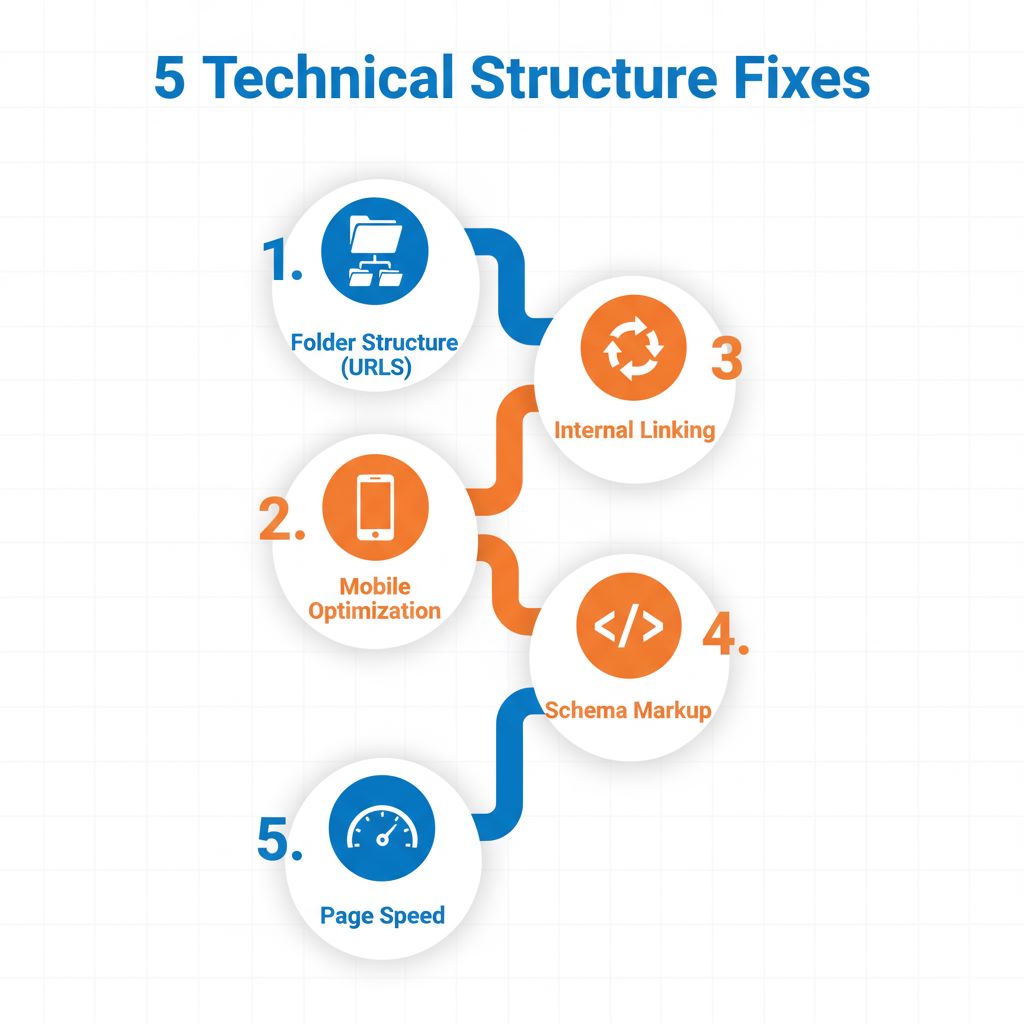

A hand drawn diagram illustrating five precise Local SEO fixes for Lagos website structure.
This post will explore five essential arrangement and configuration steps you can implement today. When these elements are correct, your site establishes the verifiable geographic authority necessary to overcome high local competition.
The Paramount Mandate of Verifiable Local Data
It is important to understand that local ranking is a matter of factual verification, and not just keywords. Google’s system works to present the most relevant and established local entity. When your website gives conflicting signals, the system lacks the confidence to rank your business above others that maintain data fidelity.
Consider the reality within Nigeria. Data from the Nigerian Communications Commission (NCC) consistently shows high mobile internet penetration. When a customer is searching for a service provider, perhaps a law firm in Ikoyi or a caterer in Surulere, they are usually on their phone and require immediate, precise information. When your site arrangement fails to articulate your location clearly, you simply surrender the opportunity.
1. Fix the Core Data Arrangement: NAP Consistency Across Your Digital Footprint
The foundation of any successful local ranking is NAP consistency. NAP stands for Name, Address, and Phone Number. This is a critical arrangement point you need to focus on.


Ensuring Content Consistency on Mobile to master mobile-first indexing for local search.
Everywhere your business appears online, your website, your Google Business Profile (GBP), and third-party directories, the NAP details must be exactly the same. Even small variations, such as using “St.” instead of “Street,” or different phone number formats, introduce ambiguity for Google’s verification system.
You must implement these steps:
- Establish a Master Record: Define the single, formal version of your business name, address, and primary contact number.
- Header and Footer Integration: Ensure the exact Master Record is text-based and visible in the header and footer of every page on your website.
- GBP Synchronization: The address on your website’s contact page must match the address used to verify your business on Google Business Profile, down to the punctuation.
This consistency is a fundamental local SEO fix for Lagos because it confirms that your digital presence references a single, verifiable physical location.
2. Implement the LocalBusiness Schema Markup Arrangement
Beyond having the NAP visible, you need to structure this data in a language search engines can process instantly. This is where LocalBusiness Schema Markup comes in.
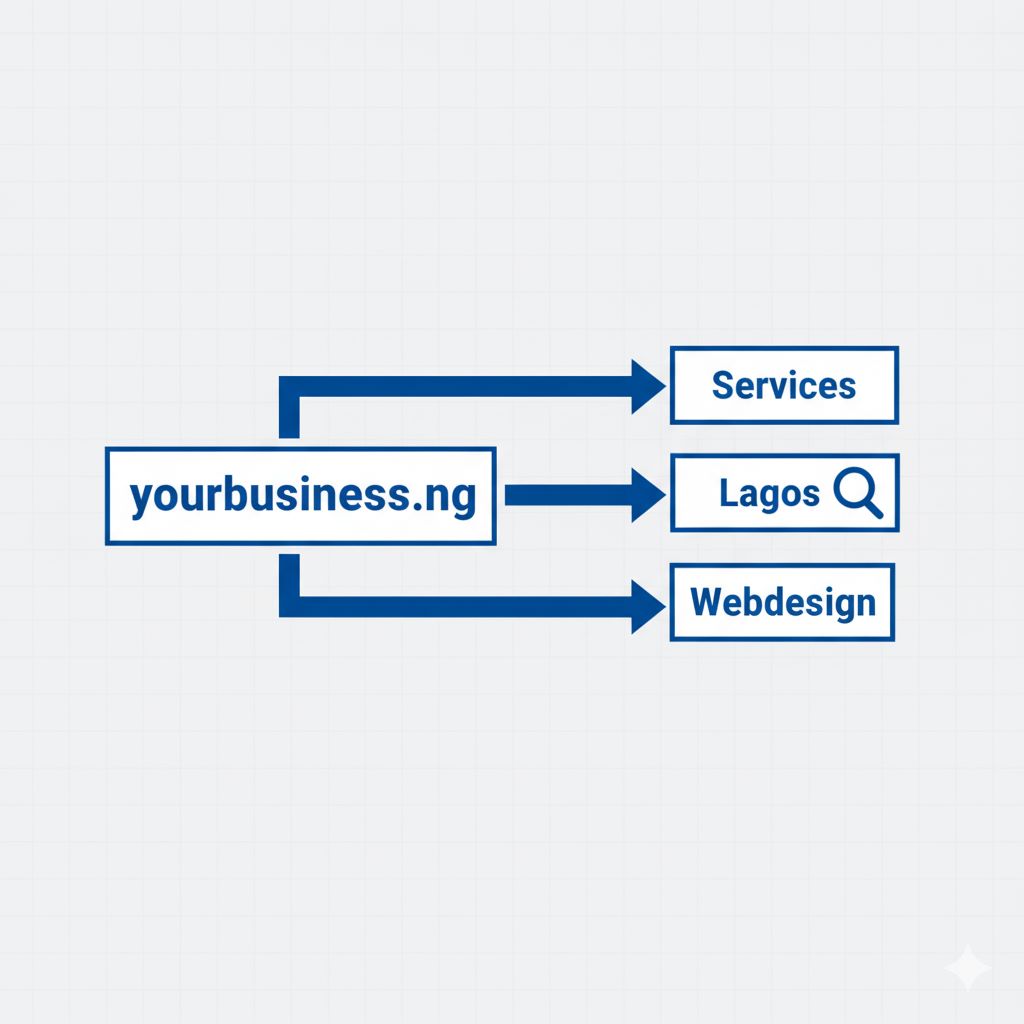

Visualizing the Geo-Specific Subdirectories structure for Local SEO Fixes for Lagos.
This technical arrangement involves placing specific code on your contact pages and your home page. This code explicitly tells search engines: “This is the name of the business, this is its verifiable address, and these are its operating hours.”
You should arrange this information directly, and not rely on Google guessing this information from text alone. We now need to ensure the following fields are accurately captured within the schema code:
@type: (e.g.,LocalBusiness,Organization, or a more specific type likeAttorney)name: The official business name.address: The full, consistent physical address.geo: The latitude and longitude of your physical location (highly precise arrangement).
When this schema is correctly arranged, your website speaks directly to the search engine’s ranking algorithm, boosting the confidence level the engine has in your local identity.
3. Arrange Service Content via Geo-Targeted Service Area Pages
When your business serves all of Lagos, simply listing “Lagos” is too vague. To overcome competitors, you must demonstrate relevance within specific neighborhoods. This is accomplished by arranging geo-targeted service area pages.
A web development firm serving the region, for instance, should have separate, focused pages such as:
- “E-commerce Development for Businesses in Ikeja“
- “Web Application Solutions for Startups in Lekki“
- “Website Maintenance for Organizations in Apapa“
Each of these pages must feature unique, relevant content about the services delivered in that specific locality. The local keyword phrase is used naturally in the headline and throughout the body text, and a map showing the coverage area can be integrated. This content arrangement is a powerful local SEO fix for Lagos because it targets the highly specific user search intent for micro-local areas.
4. Prioritize Mobile Speed and User Arrangement on Entry
You get the point, yes? Most Nigerian consumers are searching on mobile devices. A website that loads slowly or provides a poor mobile user arrangement experiences automatic penalty in local search rankings.
Google prioritizes sites that load quickly because the user experience is paramount. This is a technical arrangement, and not just a design feature.
Focus on these performance elements:
- Image Compression: Ensure all high-resolution images are compressed for rapid mobile loading with clear clarity.
- Server Response: Ensure your hosting environment offers a swift response time, particularly critical for local traffic.
- Clear Mobile Layout: The mobile version of your site must have click-friendly buttons, clear navigation, and legible text, as a poor arrangement here leads to higher bounce rates.
When your website is fast and easily navigable on mobile, you send a direct positive signal to the search engine, which translates to an improved local visibility rating.
5. Optimize Internal Link Arrangement for Geo-Relevance
The way your pages connect internally influences how search engines understand your site’s operational focus. For local SEO, you need to use internal links to connect your geo-targeted pages to your primary contact pages.
This internal link arrangement ensures that the authority of your primary domain flows directly to your localized service pages.
For example:
- On your general “Services” page, link directly to your “Lekki E-commerce Development” page using the anchor text: “Lekki E-commerce Development.”
- On your blog posts, whenever you mention a Lagos locality or industry, link back to the relevant geo-targeted service page.
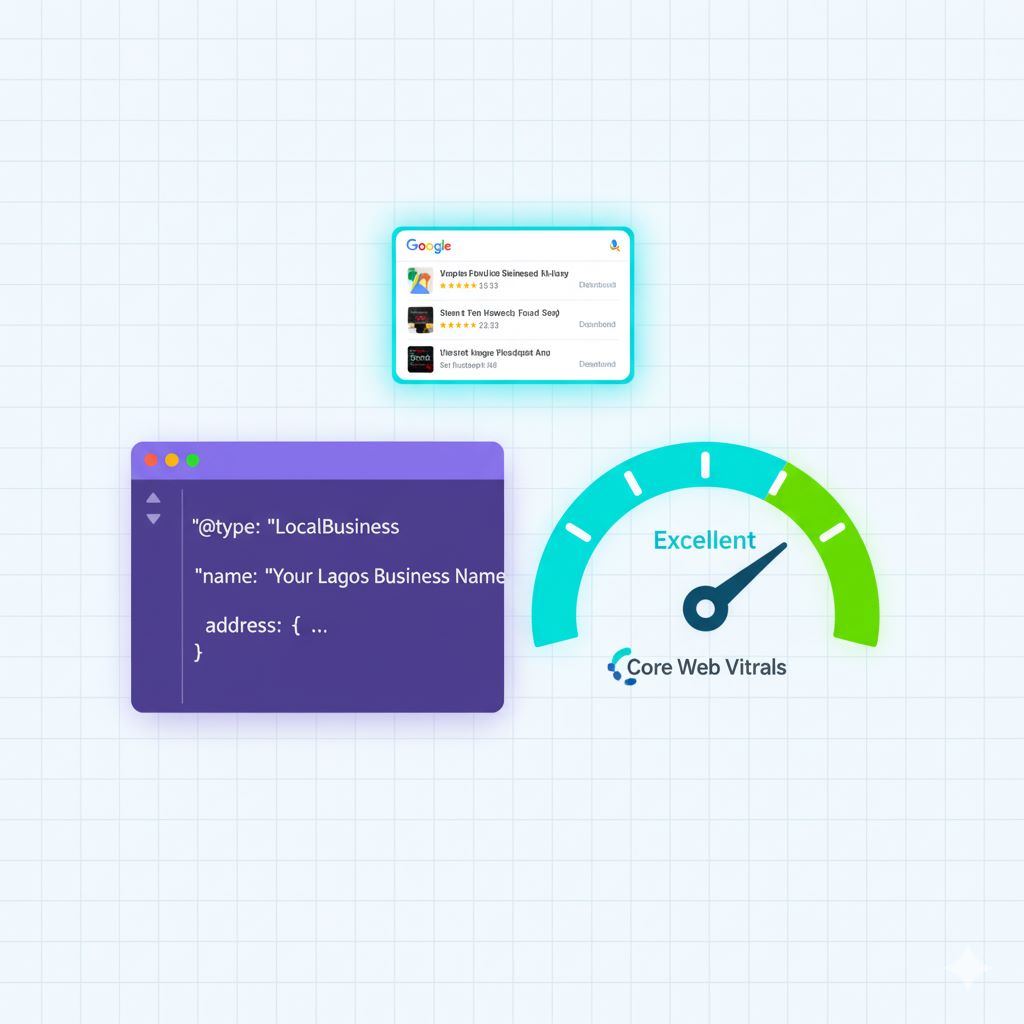

The combined impact of LocalBusiness Schema and high Page Speed on SERP dominance.
This process establishes a tight web of internal references, reinforcing your geo-relevance and making your local SEO fixes for Lagos far more effective.
If you are serious about standing out in this market, you must treat your website’s technical arrangement as a priority. Go Beyond Local is available to discuss how a technically sound, performance-focused website arrangement can deliver the geo-relevance your business requires.
Your Partner for Smart Digital, Creative & Publishing Solutions.
Uncategorized
Stop Being Busy, Start Being Productive – Focus on What Matters to Achieve Success
Uncategorized
How One Misplaced Dot Broke a Bank Login Page


A bank login page is more than just a simple screen on a website. It is the secure doorway that allows customers to reach their online accounts. Every time someone enters their username and password, the page serves as the bridge that connects the user with their money. When this page works perfectly, people enjoy smooth access. When it fails, confusion rises, and trust is shaken. What many do not know is that even a small detail, as tiny as a dot in computer code, can decide whether this door remains open or completely shut. There was a day when one misplaced dot broke a bank login page and locked out thousands of customers.
In daily life, a dot may look ordinary, simply ending a sentence. But in programming, a dot carries a higher weight. It links commands, guides actions, and connects pathways inside the code. Every dot has a position where it belongs. If that dot shifts, the whole meaning of the code changes. When the dot sits correctly, the instructions flow smoothly, and systems stay strong. But when it stands in the wrong place, the connection breaks, and the page collapses. This was exactly what happened in that bank login page error. A small misplaced dot blocked access and turned the page into a wall instead of a door.
When customers tried to log in, the page rejected every password, even when the details were correct. Error messages flashed, and people believed their accounts had been blocked. In truth, the accounts were safe, but the login script had lost its way. The misplaced dot confused the code, stopping it from speaking with the main server. What seemed like a massive cyber-attack was nothing more than a hidden syntax error. This error was small in size but great in effect. It proves once again that even a tiny seed can grow into a tree that affects many lives. In the same way, one symbol in the wrong place affected thousands of customers in one day.
The technical team of the bank was forced into action. They began a deep review of the code, reading line after line like scribes searching for a missing mark. At last, they found it. A single dot stood in the wrong place. It looked harmless, but it was the stone in the engine. Once the dot was moved back into its correct position, the entire bank login page came alive again. Customers could access their accounts, and the noise of fear began to fade. That correction, though small, restored confidence. It is a clear picture of how a little mistake can block the path, and a little correction can restore the light.
For developers and financial institutions, this case shines a light on three truths. First, it shows the necessity of code review. When more than one pair of eyes checks the script, hidden faults are easily discovered. The misplaced dot slipped through the first check, but a second review could have stopped the crisis before it began. Second, it reveals the value of a testing environment. This is a space where the system can be tested with fake accounts before it meets real customers. If the login page had gone through stronger testing, the dot would have been caught in silence. Third, it proves that every small detail matters in digital security. While banks build firewalls and strong encryption to fight hackers, they must also protect against simple human mistakes. A misplaced dot costs nothing to fix but can cost everything in customer trust.
For ordinary users, this story uncovers the hidden world behind every online banking login. People see only a clean page where they type details, but behind that page is a chain of codes stretching like an invisible ladder. If even one step on that ladder breaks, the climb becomes impossible. Customers should understand that many errors come from technical mistakes, not always from hackers. This knowledge reduces panic and allows patience while systems recover. But for the bank staff, the story is a strong call that the trust of the people rests on their attention to detail. When they watch carefully over every line of code, they protect not just data but also peace of mind.
The world of computing has seen many similar cases. Programmers call such mistakes bugs in software. Some are small, like this misplaced dot, while others are larger, like missing blocks of instructions. Yet both small and large bugs can shut down big systems. History records failures in air traffic control, hospital records, and government websites caused by such mistakes. Each time, people faced delays, stress, and fear until the error was corrected. The misplaced dot in the bank login page is only one example, but it is a sharp signal that technology is both powerful and fragile. The smallest detail carries weight, and carelessness carries a price.
The solution lies in discipline. Developers must write code with patience, treating every symbol with respect. Banks must insist on quality checks, demanding code reviews as part of their daily culture. Automated scanning tools exist today that can identify misplaced symbols and prevent errors. Regular updates and reviews make systems stronger. Training new programmers to value accuracy ensures the future remains secure. Just as a faithful servant proves trustworthy in little things, programmers who are faithful in small marks protect the greater system. In technology, faithfulness in details is not an option, it is the foundation.
This story also brings out the importance of humility in technology. The error was not a mighty attack from the outside. It was a human mistake from within. Accepting that mistakes will happen encourages the building of safety nets. Backup systems, error logs, and fallback pages are like guards that catch the fault before it spreads. When banks respect these measures, customers enjoy steady access, and confidence grows stronger. A working bank login page may appear simple on the surface, but behind it is a constant war against errors. Every line of code is part of that battle, and every symbol is a soldier.
The truth is clear. In life and in code, little things matter. Just as a spark can light up a forest, so can a misplaced dot stop an entire system. The day a dot broke a bank login page, thousands of customers were locked out. Yet the day it was corrected, peace was restored. This is the reality of technology, that strength lies in details, and confidence is built on discipline. Banks that guard their systems with careful eyes will continue to hold the trust of their people. Developers that respect every symbol will continue to create systems that stand firm. And customers who understand the hidden structure behind the screen will face errors with calm hearts, knowing that sometimes the smallest fix brings the greatest relief.
In conclusion, one misplaced dot was enough to break a bank login page. The dot changed the meaning of the code, blocked the server connection, and locked out thousands of customers. Yet, the solution was simply to place it back where it belonged. The story carries a strong signal for developers, banks, and customers alike. It proves that small details in digital banking security can have large effects in reality. When banks respect details, customers enjoy trust. When developers respect symbols, systems remain alive. And when everyone values accuracy, technology continues to serve with strength and stability.
Uncategorized
Nigerian Hackers: The Global Fraud Story and Its Fallout


The Story of Nigerian Hackers That Shook the World
The story of Nigerian hackers is one of the most unforgettable tales in the digital age. It is a record of how technology in the wrong hands can create waves across nations and shake mighty institutions. It is also a call for deeper wisdom, because when light enters darkness, nothing can remain hidden.
The global stage first began to hear about Nigerian hackers in the late 1990s and early 2000s. At that time, internet use was spreading quickly, but many people had little knowledge of online dangers. In that environment, groups of young Nigerians discovered that simple email messages could open doors to money. They crafted letters that promised sudden wealth, business opportunities, or love. These emails requested personal information or even small payments from strangers abroad. Many people believed and responded, and from there the scams grew. This practice later became famous as the “Nigerian Prince” scam. It looked simple, but it was powerful enough to shake global trust in email.
As years passed, cybercrime in Nigeria became more advanced. By the 2010s, it had grown far beyond email fraud. Hackers began to build fake websites, attack company databases, and use stolen credit card details to shop or move money. They built global networks that stretched across Europe, Asia, and America. Some even linked with international crime groups. The shock was that many of these hackers were young men, often with little formal training, yet they could break into systems that belonged to giant companies and governments. It showed the world a deeper truth, that even the small can confuse the strong.
One case that captured attention was the fall of Obinwanne Okeke (Invictus Obi). He was once celebrated as a bright young African entrepreneur and had even been listed by respected magazines as a model of success. Yet, in 2019, he was arrested in the United States and charged with fraud. Investigations revealed that his group had stolen millions of dollars from American companies through hacking and email compromise. His downfall became a headline because it showed how far Nigerian hackers had gone in infiltrating global businesses.
Another side of the story was the rise of the “Yahoo Boys.” This name came from the early days when Yahoo Mail was the platform of choice for scam messages. Over time, it became a cultural tag in Nigeria. Many of these young men were in their twenties or thirties. They became famous for driving expensive cars, wearing flashy designer outfits, and spending recklessly in public. Behind the glamour was a dark foundation of romance scams, stolen cards, and deceitful schemes. Their lifestyle made them visible, both to local communities and to international authorities. Some observers called it greed, while others saw it as a cry for survival in an economy with limited jobs.
By 2019, global authorities were already on high alert. The FBI, Interpol, and the EFCC in Nigeria began to work together. One of the biggest breakthroughs came with “Operation reWired,” where more than 200 suspects were arrested across different countries, including over 70 in Nigeria. It was one of the largest coordinated crackdowns on cybercrime. This operation proved that global cybercrime from Nigeria was real, massive, and too big to ignore.
The methods used by these hackers were equally shocking. One of the most dangerous was called Business Email Compromise (BEC). In this system, hackers gained access to the email account of a worker in a company. From there, they sent fake invoices or payment instructions to business partners. Because the email looked genuine, many companies sent millions of dollars to fraudulent accounts before they realized the deception. This type of attack affected businesses in the United States, United Kingdom, Asia, and other regions, making it one of the most damaging cybercrime strategies in the world.
The story also opened wider discussions about poverty, youth, and opportunity. Nigeria is a nation with over 200 million people, and most of them are young. Opportunities are limited, and graduates often face struggles. Some of these youths turned to cybercrime in Nigeria because they believed it was a faster route to wealth. Yet the gain was temporary, because many ended up in prison. This showed people the eternal truth that a man reaps what he sows.
But even while cybercrime created a negative picture, another side of Nigerian youth was rising. The same nation that produced Yahoo Boys also produced world-class fintech innovators, software developers, and digital start-ups. Nigerian technology hubs in Lagos, Abuja, and Port Harcourt began to show the creative power of the youth when guided in the right direction. While some chose destruction, others chose construction. This balance is necessary when telling the story of Nigerian hackers , because it is also a story of redemption and new possibilities.
The shock of these hackers forced banks, companies, and governments to strengthen their defenses. Two-factor authentication, stronger firewalls, and staff cybersecurity training became standard practice. Many organizations invested heavily in better monitoring systems. Losses caused by Nigerian hackers became the push that forced a global upgrade in digital safety. Out of the ashes of failure came lessons that built stronger foundations.
The Nigerian government also responded to the pressure. The EFCC increased raids, arrests, and prosecutions. In major cities like Lagos, Abuja, and Port Harcourt, reports of arrests filled the headlines often. These actions were important in restoring trust. Yet, as new hackers kept rising, the battle continued. Crime always grows quickly in places where opportunity is wide but discipline is weak, just like weeds sprout easily in an open field.
This wave of cybercrime also shaped how the world viewed Nigeria. On one side, the nation was celebrated for music, films, and creativity. On the other side, Nigerian hackers created suspicion that affected honest Nigerians abroad. Embassies and visa offices increased checks, and companies abroad sometimes hesitated to work with Nigerians. This was one of the silent burdens created by cybercrime.
To change the tide, education and awareness became necessary. Nigerian universities introduced cybersecurity courses. Non-profit groups started awareness campaigns to teach safe online behavior. Tech firms opened internships to redirect young talent into productive work. The goal was to transform youthful energy from destruction into construction.
Looking back, the story of Nigerian hackers is not only about fraud. It is also about how societies react to danger. It teaches the need for stronger values, fairer opportunities, and better global cooperation. It also proves that desire for fast wealth without discipline leads to collapse. A house built on sand may look strong, but it cannot endure storms.
Today, many hackers have been jailed, but cybercrime is still present in Nigeria and across the world. Yet the shock created by these events forced leaders, businesses, and communities to be more alert. The story will remain a reference point in the history of global cybersecurity.
Technology is a gift that opens doors to progress. But it must be guided with honesty and discipline. The future depends on raising strong walls, both in the digital space and in daily life. With wisdom, the same skills that once shook the world can build a brighter path for generations to come.



 Uncategorized6 hours ago
Uncategorized6 hours agoInternet Sovereignty: Why Some Countries Want Their Own Separate Internet



 Uncategorized6 hours ago
Uncategorized6 hours agoThe Smallest Change That Will Affect All Digital Operations



 Uncategorized6 hours ago
Uncategorized6 hours agoHow One Misplaced Dot Broke a Bank Login Page



 Uncategorized6 hours ago
Uncategorized6 hours agoThe Untold Story Of The Nigerian Who Helped Build Global Internet Systems



 Uncategorized6 hours ago
Uncategorized6 hours agoNigerian Hackers: The Global Fraud Story and Its Fallout



 Uncategorized6 hours ago
Uncategorized6 hours agoForgotten Satellites Defy Silence, Beaming Signals for Decades



 E-Commerce6 hours ago
E-Commerce6 hours agoDo Not Allow Your Digital Store to Shut Down:



 World on Fire6 hours ago
World on Fire6 hours agoNigeria Enter One Chance? Insecurity and Sachet Economy in 2026









