Edutech Portal
Core Web Vitals Checklist: How to Achieve a Near-Perfect Score on Mobile Devices

The Core Web Vitals Checklist: How to Achieve a Near-Perfect Score on Mobile Devices
In today’s digital economy, the speed and responsiveness of your website are are fundamental requirements for appearing in search results. Google mandates adherence to Core Web Vitals (CWV) metrics, particularly for mobile experiences. A low score on these metrics directly hinders your discoverability and affects user satisfaction. Honestly, you must consider that optimizing your site for CWV is the most essential step toward high performance.
This post will walk you through five crucial technical adjustments you need to implement. When these elements are properly configured, your website achieves the performance rating necessary to overcome the speed challenges inherent in mobile browsing across Nigeria and globally.
Understanding the Essential Performance Focus
It is important to understand that Core Web Vitals measure three specific aspects of user experience: loading, interactivity, and visual stability. These are not arbitrary metrics; they represent how a human being perceives your site’s functionality.
The focus is paramount:
- Loading: Measured by Largest Contentful Paint (LCP). This is the time it takes for the largest element (usually an image or block of text) on your page to become visible. A slow LCP means the user waits too long to see the primary content.
- Interactivity: Measured by First Input Delay (FID). This tracks the time from when a user first interacts with your page (e.g., clicks a button) to when the browser actually responds. A high FID means the user experiences lag.
- Visual Stability: Measured by Cumulative Layout Shift (CLS). This monitors unexpected shifts of page elements while the page is still loading, preventing users from clicking what they intend to click.
To achieve a near-perfect mobile score, you must address each of these three areas with technical precision.
1. Address LCP: Prioritize the Critical Rendering Path
The Largest Contentful Paint (LCP) often presents the biggest challenge. To gain a strong score, you must deliver the largest content element—usually a hero image or headline text block—in under 2.5 seconds.
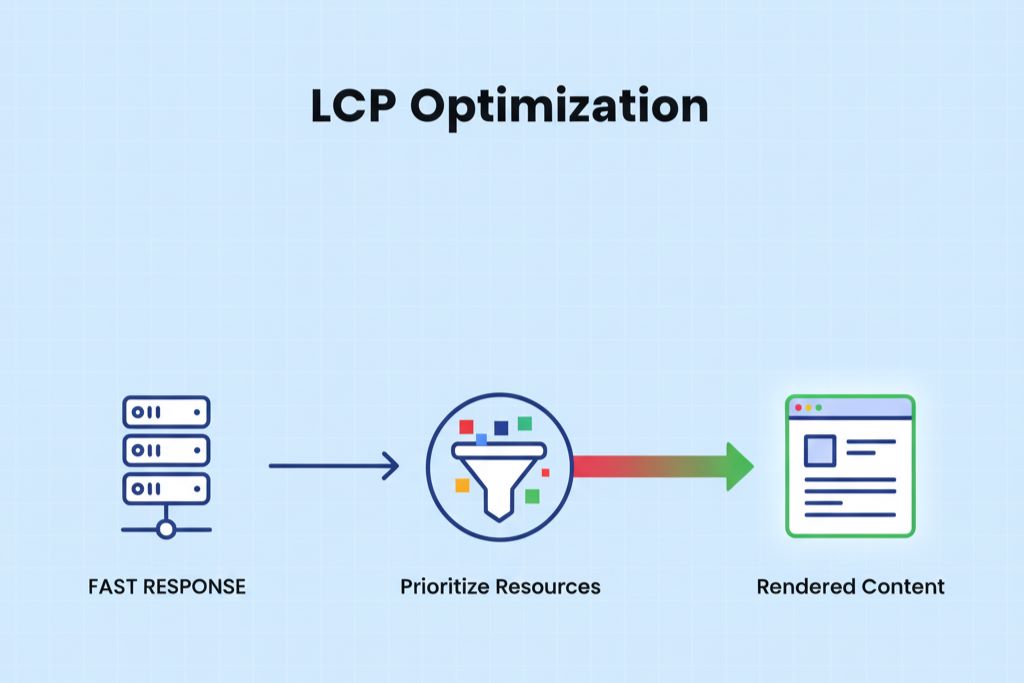

- Server Response Optimization: Ensure your server response time is swift. This means leveraging quality hosting infrastructure. Go Beyond Local can assist in evaluating and configuring high-speed hosting solutions available for your region.
- Resource Prioritization: Identify and defer the loading of any non-essential Cascading Style Sheets (CSS) or JavaScript files that appear before the main content. Only the absolute minimum code required to render the LCP element should be loaded first.
- Image Compression and Sizing: The largest image on your page should be served in the correct dimensions for the device and heavily compressed. Use modern formats like WebP where possible, as they offer superior compression.
When you optimize the critical rendering path, the user sees the primary page content rapidly, leading to an immediate improvement in the LCP score.
2. Overcome FID: Break Up Long JavaScript Tasks
You get the point, yes? When the browser is busy processing a massive block of JavaScript code, it cannot respond to user input. That lag is what generates a poor First Input Delay (FID).
To overcome this difficulty, the main thread needs to be available quickly. We now need to ensure the following:
- Code Splitting: Divide large JavaScript bundles into smaller, focused chunks. Load these chunks only when they are needed for a specific function, rather than all at once on initial page load.
- Third-Party Script Management: Limit the number of external scripts (like analytics, ads, or social widgets). When you must use them, load them lazily (only when they enter the viewport) or defer them to run after the main page content is interactive.
- Web Workers: Where heavy processing is mandatory, such as complex data handling, leverage Web Workers. This ensures those processes run in the background, keeping the main browser thread free for immediate user interaction.
Honestly, reducing the amount of time the main thread is blocked is the most direct path to a near-perfect FID score.
3. Mitigate CLS: Reserve Space for Dynamic Elements
Unexpected shifts in the layout (CLS) cause frustration; users click something, and the element moves right as the click registers. This issue often results from dynamic content, like ads or embedded videos, loading without reserved space.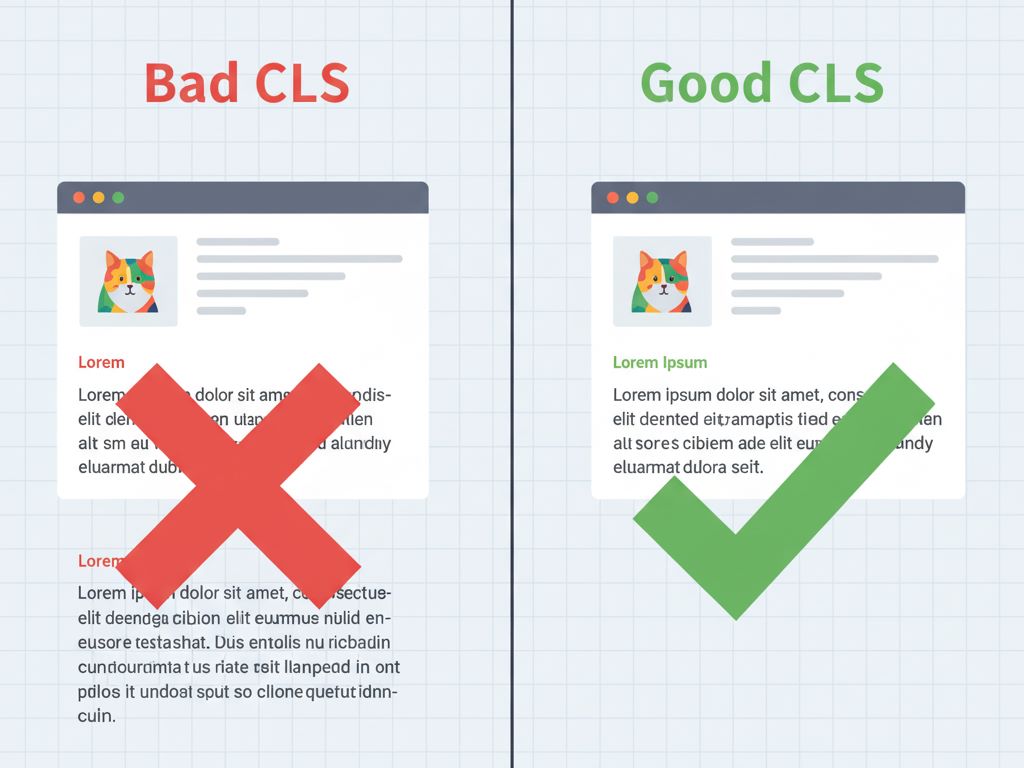

We must address this instability with precision:
- Explicit Dimensions: Always include width and height attributes on images and video elements. This tells the browser exactly how much space to reserve before the content loads, preventing surrounding elements from shifting.
- Font Loading Strategy: Fonts loaded from external sources can cause a shift when the fallback font is suddenly replaced. Use a
font-display: optionalorswapstrategy to manage this transition gracefully, and ensure text stays in place. - Avoid Uninjected Content: Avoid inserting new elements above existing content unless a user action triggers it. This practice forces the entire page to rearrange, which directly increases the CLS score.
When you properly reserve space for all elements, you deliver a stable visual experience, which is crucial for a positive mobile interaction.
4. Leverage Browser Caching for Repeat Visits
It is a known fact that users often return to websites that offer valuable services. For these repeat visits, browser caching is an essential optimization.
Caching instructs the user’s browser to store local copies of static assets (images, CSS, fonts). On a subsequent visit, the browser loads these assets directly from the local device, bypassing the network request. This immediately and drastically reduces the loading time for repeat users, which positively affects all three CWV metrics.
You should focus on caching directives:
- Expiration Headers: Implement appropriate
Cache-Controlheaders on your server to define how long the browser should store static assets. - Asset Fingerprinting: When you update an asset (like a CSS file), ensure its file name changes (e.g.,
styles-v2.css). This forces the browser to fetch the new version while retaining the cache for all other files.
Leveraging this technology helps you maintain high performance, particularly on slower networks prevalent in some parts of the region.
5. Review and Compress CSS for Efficiency
Even after optimizing JavaScript, you need to turn your focus to Cascading Style Sheets (CSS). Unnecessarily large or poorly written CSS files delay rendering and consume valuable network bandwidth.
Honestly, you must reduce the file size of your CSS:
- Minification: Remove all non-essential characters from your CSS files, including comments and white space. This makes the file lighter without changing its function.
- Eliminate Unused CSS: Many templates load code for elements that are never used on the page. Tools are available to identify and remove this dead code, ensuring only necessary styling is loaded. This is a highly effective way to gain faster initial load times.

Your Partner for Smart Digital, Creative & Publishing Solutions.
Edutech Portal
Nigerian Hackers: The Global Fraud Story and Its Fallout


The Story of Nigerian Hackers That Shook the World
The story of Nigerian hackers is one of the most unforgettable tales in the digital age. It is a record of how technology in the wrong hands can create waves across nations and shake mighty institutions. It is also a call for deeper wisdom, because when light enters darkness, nothing can remain hidden.
The global stage first began to hear about Nigerian hackers in the late 1990s and early 2000s. At that time, internet use was spreading quickly, but many people had little knowledge of online dangers. In that environment, groups of young Nigerians discovered that simple email messages could open doors to money. They crafted letters that promised sudden wealth, business opportunities, or love. These emails requested personal information or even small payments from strangers abroad. Many people believed and responded, and from there the scams grew. This practice later became famous as the “Nigerian Prince” scam. It looked simple, but it was powerful enough to shake global trust in email.
As years passed, cybercrime in Nigeria became more advanced. By the 2010s, it had grown far beyond email fraud. Hackers began to build fake websites, attack company databases, and use stolen credit card details to shop or move money. They built global networks that stretched across Europe, Asia, and America. Some even linked with international crime groups. The shock was that many of these hackers were young men, often with little formal training, yet they could break into systems that belonged to giant companies and governments. It showed the world a deeper truth, that even the small can confuse the strong.
One case that captured attention was the fall of Obinwanne Okeke (Invictus Obi). He was once celebrated as a bright young African entrepreneur and had even been listed by respected magazines as a model of success. Yet, in 2019, he was arrested in the United States and charged with fraud. Investigations revealed that his group had stolen millions of dollars from American companies through hacking and email compromise. His downfall became a headline because it showed how far Nigerian hackers had gone in infiltrating global businesses.
Another side of the story was the rise of the “Yahoo Boys.” This name came from the early days when Yahoo Mail was the platform of choice for scam messages. Over time, it became a cultural tag in Nigeria. Many of these young men were in their twenties or thirties. They became famous for driving expensive cars, wearing flashy designer outfits, and spending recklessly in public. Behind the glamour was a dark foundation of romance scams, stolen cards, and deceitful schemes. Their lifestyle made them visible, both to local communities and to international authorities. Some observers called it greed, while others saw it as a cry for survival in an economy with limited jobs.
By 2019, global authorities were already on high alert. The FBI, Interpol, and the EFCC in Nigeria began to work together. One of the biggest breakthroughs came with “Operation reWired,” where more than 200 suspects were arrested across different countries, including over 70 in Nigeria. It was one of the largest coordinated crackdowns on cybercrime. This operation proved that global cybercrime from Nigeria was real, massive, and too big to ignore.
The methods used by these hackers were equally shocking. One of the most dangerous was called Business Email Compromise (BEC). In this system, hackers gained access to the email account of a worker in a company. From there, they sent fake invoices or payment instructions to business partners. Because the email looked genuine, many companies sent millions of dollars to fraudulent accounts before they realized the deception. This type of attack affected businesses in the United States, United Kingdom, Asia, and other regions, making it one of the most damaging cybercrime strategies in the world.
The story also opened wider discussions about poverty, youth, and opportunity. Nigeria is a nation with over 200 million people, and most of them are young. Opportunities are limited, and graduates often face struggles. Some of these youths turned to cybercrime in Nigeria because they believed it was a faster route to wealth. Yet the gain was temporary, because many ended up in prison. This showed people the eternal truth that a man reaps what he sows.
But even while cybercrime created a negative picture, another side of Nigerian youth was rising. The same nation that produced Yahoo Boys also produced world-class fintech innovators, software developers, and digital start-ups. Nigerian technology hubs in Lagos, Abuja, and Port Harcourt began to show the creative power of the youth when guided in the right direction. While some chose destruction, others chose construction. This balance is necessary when telling the story of Nigerian hackers , because it is also a story of redemption and new possibilities.
The shock of these hackers forced banks, companies, and governments to strengthen their defenses. Two-factor authentication, stronger firewalls, and staff cybersecurity training became standard practice. Many organizations invested heavily in better monitoring systems. Losses caused by Nigerian hackers became the push that forced a global upgrade in digital safety. Out of the ashes of failure came lessons that built stronger foundations.
The Nigerian government also responded to the pressure. The EFCC increased raids, arrests, and prosecutions. In major cities like Lagos, Abuja, and Port Harcourt, reports of arrests filled the headlines often. These actions were important in restoring trust. Yet, as new hackers kept rising, the battle continued. Crime always grows quickly in places where opportunity is wide but discipline is weak, just like weeds sprout easily in an open field.
This wave of cybercrime also shaped how the world viewed Nigeria. On one side, the nation was celebrated for music, films, and creativity. On the other side, Nigerian hackers created suspicion that affected honest Nigerians abroad. Embassies and visa offices increased checks, and companies abroad sometimes hesitated to work with Nigerians. This was one of the silent burdens created by cybercrime.
To change the tide, education and awareness became necessary. Nigerian universities introduced cybersecurity courses. Non-profit groups started awareness campaigns to teach safe online behavior. Tech firms opened internships to redirect young talent into productive work. The goal was to transform youthful energy from destruction into construction.
Looking back, the story of Nigerian hackers is not only about fraud. It is also about how societies react to danger. It teaches the need for stronger values, fairer opportunities, and better global cooperation. It also proves that desire for fast wealth without discipline leads to collapse. A house built on sand may look strong, but it cannot endure storms.
Today, many hackers have been jailed, but cybercrime is still present in Nigeria and across the world. Yet the shock created by these events forced leaders, businesses, and communities to be more alert. The story will remain a reference point in the history of global cybersecurity.
Technology is a gift that opens doors to progress. But it must be guided with honesty and discipline. The future depends on raising strong walls, both in the digital space and in daily life. With wisdom, the same skills that once shook the world can build a brighter path for generations to come.
Edutech Portal
Internet Sovereignty: Why Some Countries Want Their Own Separate Internet


Why Nations Build Independent Networks
The question of why some countries desire their own Internet has become louder in recent years. Around the world, governments and leaders are moving towards what many describe as Internet sovereignty. This is the idea that a nation can create its own controlled system, a digital territory that functions within its borders while still having selective links to the wider world. It is like building a strong city with gates that open only when the guards allow. For these nations, a separate Internet represents strength, safety, and independence.
One of the most powerful reasons is cybersecurity. Leaders believe that the global Internet exposes their citizens to unnecessary risks. Cyberattacks, digital spying, and online crime have grown at alarming levels. By creating a system that works internally, governments can protect sensitive data and shield people from outside harm. It is like fortifying a home so that even in stormy weather, the family inside remains secure. In this way, a national Internet becomes a shield against the invisible battles that rage in the digital space.
Political control also drives this decision. Many governments argue that foreign platforms spread information that weakens their authority. They feel that hostile voices use the global Internet to influence local minds. By managing their own digital territory, they can guide conversations, control online media, and set boundaries. It is similar to ancient kings who guarded their city gates, not out of fear, but out of duty to protect the peace of their people. A separate Internet offers them the authority to defend unity within their borders.
Economic motivation is another strong pillar. At present, most of the digital economy is powered by giants from America, Europe, and China. These global platforms dominate markets, harvest data, and earn profits that flow away from local economies. Nations that build their own systems hope to establish local search engines, social media, and online stores. This keeps wealth inside the country, creates employment, and empowers local entrepreneurs. For them, digital independence is not just about control but also about prosperity that can spread to citizens through job creation and innovation.
Technology growth is deeply linked to this movement. Nations that invest in their own Internet infrastructure also create opportunities for development in data centers, fiber cables, servers, and even satellites. These investments build national capacity and open doors for local innovation. Young developers can create platforms in their own language, rooted in their own culture, and aligned with the habits of their people. This is how technology becomes a tool for both empowerment and education. A national Internet project therefore helps build a foundation for long-term growth.
Culture plays a central role as well. The global Internet often promotes the values of bigger nations, which sometimes erode smaller cultural identities. By establishing their own digital systems, countries preserve language, heritage, and traditions. They can create safe platforms for children, encourage family-centered content, and protect social values. Leaders see cultural protection as essential to survival, because a nation that forgets its roots may lose its way. A local Internet system is seen as a guardian of heritage in the digital age.
The matter of false information adds more urgency. Across the world, harmful news and online manipulation spread quickly on global platforms. Governments argue that external companies rarely solve the problem fully. With a separate Internet, they can enforce laws more easily, regulate harmful content, and give more space to truth. By doing this, they hope to reduce confusion and strengthen unity among their people. For them, information control is not censorship but protection from the chaos that unchecked lies can cause.
Independence from foreign infrastructure is another factor. The Internet relies on the Domain Name System (DNS), which is managed largely from the United States. Some nations are uneasy depending on a foreign power for such an essential service. They see the creation of their own root servers as a way to guarantee survival even in times of conflict. It is like digging a personal well of water so that even if the main supply is cut, the people still drink. This explains why some countries now explore building their own Internet backbone.
Examples already exist. China controls its digital space through what many call the Great Firewall, blocking foreign websites while promoting local alternatives. Russia has tested disconnection from the global Internet to ensure its sovereign system functions independently. Iran continues to expand its National Information Network, designed to keep activity local. These nations show that the movement towards Internet sovereignty is not only an idea but a living reality already in motion.
Of course, challenges remain. Building and maintaining a separate Internet requires large investment, advanced expertise, and constant updates. There are also trade-offs. Businesses may struggle to access global markets, researchers may find fewer international resources, and citizens may lose exposure to global ideas. Balancing security with openness becomes the central test. Yet many nations still prefer preparation, reasoning that it is better to store food in the time of plenty than to be empty in the day of famine.
This journey also carries a spiritual undertone. Words mold nations. Words build, and words tear down. Leaders who push for national Internets believe that their voice must ring louder among their people than foreign voices. They want to guide, protect, and guard, like shepherds who shield their flock from wolves. The Internet, therefore, becomes more than technology. It becomes an altar where truth and influence flow, and nations are determined to guard that sacred stream.
The defenders of a global Internet, led by the United States and Europe, argue that openness drives innovation, trade, and cooperation. Yet even they build stronger defenses against cyber threats. This shows that the debate is not whether control is needed but about how much control is wise. Both sides prepare, both sides invest, and both sides acknowledge the power of information in forming the future.
Citizens stand divided. Many enjoy the openness of the global Internet and fear losing it, while others prefer safety, order, and stability even at the cost of limited access. Regardless of opinion, one fact remains: the Internet touches every corner of daily life. It influences how people learn, communicate, work, and even worship. This makes the choice of a national Internet one of the most significant decisions of our time.
The path ahead may not be a single global Internet. Instead, the world may see multiple networks forming regional clusters or national blocks. These changes can affect global unity but also create new alliances. Nations with similar visions may join their systems together. Families, students, and workers will experience these shifts directly because the flow of digital information will mold their opportunities and their culture.
At the global stage, organizations like the United Nations continue discussing digital governance. They search for balance between state authority and individual freedom. But in the end, the decision rests with each nation. The trend is clear, more leaders are leaning towards Internet sovereignty, and the world is adjusting to this new reality.
The drive for a separate Internet grows from many roots: the need for security, the desire for economic independence, the protection of culture, the control of information, and the hunger for self-reliance. Some countries build for defense, others for prosperity, and many for identity. The map of the digital world may soon resemble the map of physical nations. The Internet of tomorrow will not look like the Internet of today, and nations that prepare early will mold their future with strength and confidence.
Edutech Portal
Forgotten Satellites Defy Silence, Beaming Signals for Decades


How Forgotten Satellites Still Beam Signals To Earth
Many people believe that once a satellite ends its mission, it becomes silent forever. That thought is not fully accurate. Even after decades, forgotten satellites still beam signals to Earth. Their voices may be faint, their rhythm irregular, but they still speak. This shows that works of human hands may endure far beyond their intended time, just like seeds that lie hidden and spring forth in their own season.
A satellite is a machine placed in orbit to send and receive data. Modern living depends heavily on these machines. They guide communication, navigation, weather studies, and scientific observation. When a satellite is fresh, engineers monitor it every day. They collect signals, send commands, and ensure smooth operations. As years pass, some lose power while others give way to newer technology. These are called forgotten satellites, yet forgotten does not mean lifeless.
Many satellites still remain in orbit, circling the Earth faithfully. Their solar panels continue to gather sunlight. When that light touches their circuits, small portions of power awaken old systems. That is why a forgotten satellite still beams signals to Earth. The tones may be weak, but sensitive equipment on Earth can still capture them.
In 1965, the United States launched a satellite named LES-1. It failed early and was declared useless. Engineers turned their eyes away, but almost 48 years later, amateur operators heard signals from it again. In 2013, that old machine sang once more. Its solar panels had preserved strength enough to power its radio. This story echoes that what men leave aside, heaven may still keep alive for a season.
There are other stories of old weather satellites waking when sunlight strikes them in just the right way. Some retired navigation satellites still send simple radio beacons. To the ordinary ear, these sounds are noise. To scientists, they are treasure. Every signal carries information about how machines endure in space and how materials face the harshness of radiation, heat, and cold.
The reason many of these satellites survive so long is because the space environment slows down decay. On Earth, machines rust and break quickly due to air and water. In orbit, the main threats are radiation and temperature changes. If a satellite was built with strong design, certain parts may keep functioning for decades. Solar energy is the key. As long as panels collect light, signals may still travel down to Earth.
These signals also provide testing ground for radio receivers. Operators on Earth sometimes direct their antennas at such satellites to capture faint tones. This practice sharpens listening technology for deep space missions, where signals from far planets are also very weak. It is like training the ear to hear whispers in a noisy crowd.
Old satellites also carry history. Their signals reflect the thinking of the time they were made. When engineers hear a tone from the 1960s, they are echoed back to early designs and limited tools of that age. Each signal is like the voice of an old friend, teaching how knowledge has grown from seed to tree.
Records of such satellites are kept by space agencies. Lists show which satellites are active, silent, or partly alive. Amateur groups also share reports whenever they pick signals. With modern internet, these discoveries spread quickly across the world. Scientists then confirm and celebrate that a satellite still breathes faintly in space.
There are also challenges. A forgotten satellite is no longer under command. Engineers cannot redirect it or control its orbit. It becomes part of space debris. This debris can cross paths with active satellites. Space agencies watch carefully to prevent collisions. Even so, the weak signals remain echoes that strength may still flow from vessels long abandoned.
The story of forgotten satellites carries deep lessons. Machines of men may seem finished, yet many endure. Just as human effort fades, divine purpose continues. A satellite still beaming after fifty years reveals endurance, patience, and hidden strength. These are qualities worth embracing in daily living.
From a scientific side, these signals help plan for future missions. Engineers study why certain circuits lasted so long. The knowledge guides them to build tougher machines for tomorrow. Materials that resist radiation and designs that save energy become new standards. In this way, a forgotten satellite still beams signals to Earth and continues to serve the progress of science.
Such discoveries also show global unity. Scientists in Africa, America, Europe, and Asia all share findings. A signal from a forgotten satellite becomes a joint testimony across borders. The sky has no boundaries, and its wisdom is open to all who look upward.
Students also gain inspiration. When young people learn that a satellite from 1965 still transmits, they see the power of endurance. Teachers use such examples in classrooms to stir fresh interest in science. They learn that technology is not only about today but also about lessons from the past and seeds of the future.
As the number of satellites in orbit increases each year, some will retire early while others will last for decades. Some will sleep and then rise again when sunlight awakens them. Each of them becomes part of the great circle of knowledge. Each signal is a message, however faint, echoing that nothing hidden stays silent forever.
Forgotten satellites still beam signals to Earth because solar energy revives their circuits, space slows their decay, and radio tones continue to whisper across the heavens. These signals preserve history, advance science, and inspire human hearts. They stand as witnesses that endurance is possible, and what appears finished may still serve a purpose.



 Edutech Portal1 week ago
Edutech Portal1 week agoInternet Sovereignty: Why Some Countries Want Their Own Separate Internet



 Edutech Portal1 week ago
Edutech Portal1 week agoThe Smallest Change That Will Affect All Digital Operations



 Digital Hustle1 week ago
Digital Hustle1 week agoHow One Misplaced Dot Broke a Bank Login Page



 Edutech Portal1 week ago
Edutech Portal1 week agoThe Untold Story Of The Nigerian Who Helped Build Global Internet Systems



 Edutech Portal1 week ago
Edutech Portal1 week agoNigerian Hackers: The Global Fraud Story and Its Fallout



 Edutech Portal1 week ago
Edutech Portal1 week agoForgotten Satellites Defy Silence, Beaming Signals for Decades



 Edutech Portal1 week ago
Edutech Portal1 week agoDo Not Allow Your Digital Store to Shut Down:



 Edutech Portal1 week ago
Edutech Portal1 week agoImplement Local SEO Fixes for Lagos: Beat Google Maps Competitors







